Application Security , Next-Generation Technologies & Secure Development , Security Operations
Defending Against Application Breaches
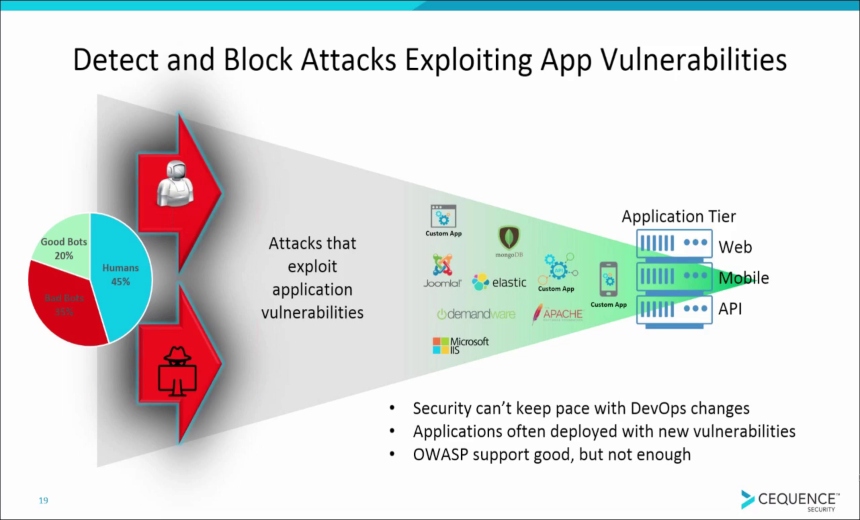
The new #1 cyber threat - attacks on the applications that power your business...In today's hyper-connected organizations, you depend on externally facing web, mobile, and API-based applications to connect with customers, partners, suppliers, and employees. These strategically important applications support business processes and enable you to create an extended, efficient digital ecosystem.
Unfortunately, these same applications have become primary targets for two vastly different, but equally dangerous, types of cyberattacks. Successful application breaches can lead to financial fraud, stolen IP, and business disruption.
Cequence Security recently completed two separate research projects with Ponemon Institute and Osterman Research, which provide insights into these attacks and defense strategies at nearly 900 organizations across the US.
Watch this video to learn:
- What the two cyberattacks are and how they're dangerous;
- How they're impacting your peers;
- What you can do to protect your hyper-connected organization.